Intro to .NET Reverse Engineering
VFTs suck (if you know you know)
You’ve got your hands on a .NET binary that you want to reverse engineer. What do you do?
You can’t just open in the Ghidra CodeBrowser like you’d normally do with an executable. Well, you could, but when you try to analyze a .NET binary in Ghidra you’ll probably get an error message that says something like Demangler Micosoft> Apply failure (DemangledFunction: IllegalArgumentException :
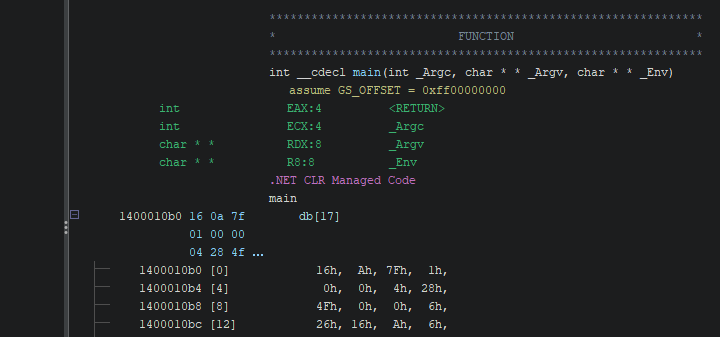
After that, you’d probably check the program entry or main function, but you would see this
or this
which are all indications that the PE you’re looking at was built using the .NET framework.
(What is .NET? Essentially it’s a framework for software engineers to build something once and run in anywhere, kind of like Java. In fact, both Java and .NET use an intermediate language that is compiled into machine code at runtime using a JIT compiler.)
At first glance it appears that Ghidra is failing to disassemble the machine code at the beginning of main, but the note above main (NET CLR Managed Code) tells us why; this isn’t machine code, it’s CIL (Common Intermediate Language) bytecode. In other words, it’s the intermediate language into which .NET programs are compiled; the CIL code isn’t compiled into assembly and then machine code until runtime by the CLR (Common Language Runtime) JIT compiler.
Tools for Disassembling .NET CIL
Ghidra’s disassembler wasn’t built to disassemble intermediate languages such as CIL, and to my knowledge no one has created a Ghidra plugin to support disassembling CIL since there are already tools that do this. For a more in depth comparison of these tools, see this article. Here’s a brief description of some of the most popular tools:
dotPeek
A .NET decompiler that is actively maintained by JetBrains with full documentation. This tutorial by JetBrains gives a quick tour around the app.
ILSpy
A very popular open source disassembler. I thought this video gave a good concise introduction to using the app.
dnSpy
This is/was also a very popular tool, but I’ve found that there’s limited documentation and tutorials online for how to use it. Additionally, the project on github was archived in 2020 and hasn’t been updated since. However, there is an unofficial fork that still receives updates as of this writing.
Try it Yourself
If you’d like some guided practice reverse engineering .NET binaries, I’d recommend checking out Nightmare’s github repository.
Further Reading
If CIL can be easily disassembled into the original source code, isn’t that a security concern? Yes. For that reason, many .NET developers use tools to obfuscate their code (though not as many as probably should). Read more about it here.